Check your Toolchain
Python is popular, and so is the problem

The Problem
User-assisted remote attackers can overwrite arbitrary files via a filename ".." sequence in TAR archives via the extract and extractall functions in the tarfile module.
A ".." sequence vulnerability is an example of directory traversal, caused by code not sanitising the given path, in this case where the module is to extract from.
SCOPE
The exploit is 15 years old.
The exploit affects some 350,000 open-source projects.
How many closed sources are affected?
The Solution
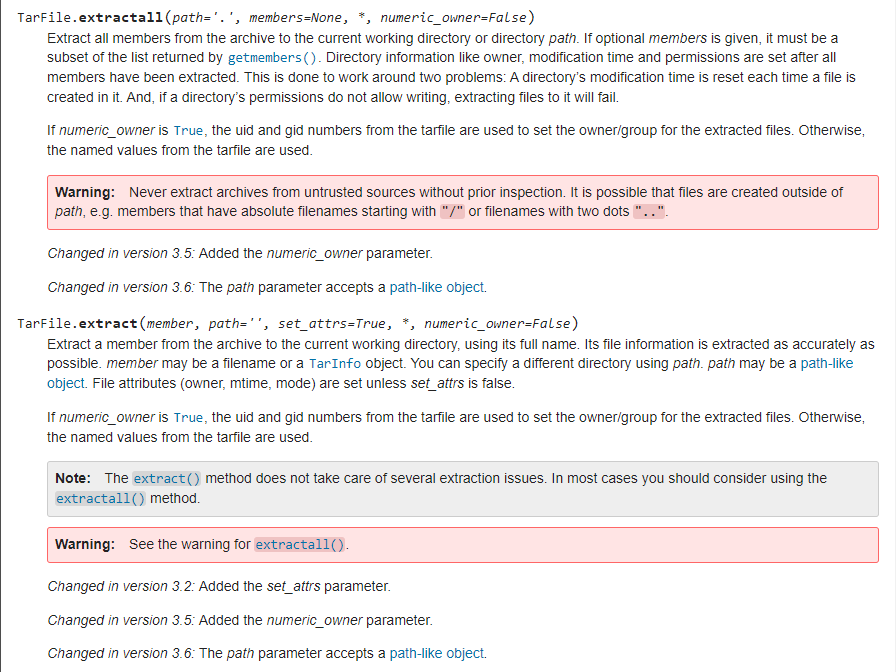
The official documentation reminds us of the obvious: don't trust unknown sources.
To automate the process, there is a recursive script that searches and scans python files for the tarfile vulnerability: Creosote


